SANS put on another spectacular challenge for us during the holiday times, the Holiday Hack Challenge! A mix of 2d mmo + security challenges : )
Starting out we see on the instruction page that we're looking for a secret message in Santa's tweets - https://twitter.com/santawclaus
This can also be seen in the introduction image of Santa's Business Card:
The tweets didn't look like much except a bunch of Christmas themed words smashed together...
Precursory thoughts lead me to believe it could be a rudimentary cipher or stego challenge of some kind. Copying all the tweets into VIM and deleting the timestamps / usernames was the first step. This instantly lead to a solution:
The next part was to look into Santa's Instagram profile. This was located here - https://www.instagram.com/santawclaus
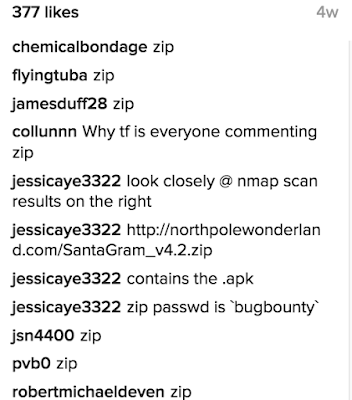
There were a couple funny images and the main one being a hacker's workspace (Most likely Santa W. Claus or an elf working for him). Scattered through-out was python reading material, SANS workshops, an nmap scan, half eaten jerky and a little peek at the screen of the user. On the laptop monitor in the top you see an interesting file SantaGram_v4.2.zip, and the scan contains an interesting url: http://www.northpolewonderland.com/.
Also in the comments, it was riddled with zip remarks (probably highlighting the mistake of leaking the filename) and a pointer to the same server with the actual file and password. Most of these accounts had no followers or posts, so they were probably setup for the challenge:
After downloading and unpacking the zip, now we have an APK to play with! Instantly disassembled and decompiled it using apktool to take a look at the source.
The next couple questions had to do with the APK:
3) What username and password are embedded in the APK file?
4) What is the name of the audible component (audio file) in the SantaGram APK file?
For #3, we can simply grep through the contents of the decompiled apk for any trace of 'password', this ended up dropping:
jSONObject.put("username", "guest");
jSONObject.put("password", "busyreindeer78");
For #4 we could just use a find and grep for mp3's / audio in the name.
$ find . |grep -i mp3 ./res/raw/discombobulatedaudio1.mp3
The next set of challenges had to do with collecting some items in-game to construct a 'Cranberry Pi' eluding to the Raspberry Pi, but ... Christmas flavored?
When talking to a character in the game after all the pieces were collected, they provided a Raspberry Pi image which relate to the next question:
5) What is the password for the "cranpi" account on the Cranberry Pi system?
This was achieved by mounting the Raspberry Pi image on a linux box, then pulling out the passwd & shadow files to crack the 'cranpi' account credentials. This was done quickly with john & rockyou.
Terminal Doors
Next up was the terminal doors, these were found through-out the 2D game which featured a terminal in-front of a locked door which would unlock when you got the key.
Elf House #2
In the game there was a building called "Elf House #2" which contained a terminal unlocking a room. Looking at the file system we see that we need to inspect a pcap. The pcap is owned by another user "Itchy". Initially your username is "Scratchy" -- most likely referencing the Simpsons in "The Itchy & Scratchy Show"
******************************************************************************* * * *To open the door, find both parts of the passphrase inside the /out.pcap file* * * ******************************************************************************* scratchy@f550041cb156:/$ ls bin dev home lib64 mnt out.pcap root sbin sys usr boot etc lib media opt proc run srv tmp var scratchy@f550041cb156:/$
Looking at the permissions we have the ability to run strings & tcpdump on the pcap.
scratchy@006599aaaf89:/$ sudo -l
sudo: unable to resolve host 006599aaaf89
Matching Defaults entries for scratchy on 006599aaaf89:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User scratchy may run the following commands on 006599aaaf89:
(itchy) NOPASSWD: /usr/sbin/tcpdump
(itchy) NOPASSWD: /usr/bin/strings
Running strings looking for longer occurrences, we find part of the key. I guessed the second half based on the theme of the game and the characters provided.
cratchy@3f9fbad1c2e2:/$ sudo -S -u itchy strings -n 40 out.pcap <input type="hidden" name="part1" value="santasli" />
In the door there was an elf providing feedback about "Copy as Curl" in Burp which was very helpful later on in the challenge.
Workshop -> DFER
******************************************************************************* * * * Find the passphrase from the wumpus. Play fair or cheat; it's up to you. * * * ******************************************************************************* elf@ee24bd520fdb:~$
This was the classic Hunt The Wumpus game. On this one I just played the game, nothing too special, but it was fun!
Workshop -> Santa's Office
This was another quick one.
First started out by using find. After that we get a listing of filenames which need a bunch of escaping to type... But we're lazy, so we'll just use grep. (Output is cut for brevity)
******************************************************************************* * * * To open the door, find the passphrase file deep in the directories. * * * ******************************************************************************* elf@a13973c497af:~$ find . ./.doormat/. / /\/\\/Don't Look Here!/You are persistent, aren't you?/'/key_for_the_do or.txt elf@a13973c497af:~$ grep -r . .doormat/. / /\/\\/Don't Look Here!/You are persistent, aren't you?/'/key_for_the_door .txt:key: open_sesame
The key ended up being 'open_sesame' -- It reminded me a lot of one of the earlier bandit challenges, over at http://overthewire.org/wargames/.
Santa's Office
This was one of my favorite discoveries on all of the terminals. The scene from WarGames played out! If you haven't seen WarGames definitely go out and grab a copy.
To get through this terminal session, all you have to do is enter the text just like the film.
You can grab the script by watching the video here - https://www.youtube.com/watch?v=-1F7vaNP9w0
GREETINGS PROFESSOR FALKEN.
Hello.
HOW ARE YOU FEELING TODAY?
I'm fine. How are you?
EXCELLENT, IT'S BEEN A LONG TIME. CAN YOU EXPLAIN THE REMOVAL OF YOUR USER ACCOUNT ON
6/23/73?
People sometimes make mistakes.
YES THEY DO. SHALL WE PLAY A GAME?
Love to. How about Global Thermonuclear War?
WOULDN'T YOU PREFER A GOOD GAME OF CHESS?
Later. Let's play Global Thermonuclear War.
FINE
...
,------~~v,_ _ _--^\
|' \ ,__/ || _/ /,_ _
/ \,/ / ,, _,,/^ v v-___
| / |'~^ \
\ | _/ _ _/^
\ / / ,~~^/ |
^~~_ _ _ / | __,, _v__\ \/
'~~, , ~ \ \ ^~ / ~ //
\/ \/ \~, ,/
~~
UNITED STATES SOVIET UNION
WHICH SIDE DO YOU WANT?
1. UNITED STATES
2. SOVIET UNION
PLEASE CHOOSE ONE:
1
AWAITING FIRST STRIKE COMMAND
-----------------------------
PLEASE LIST PRIMARY TARGETS BY
CITY AND/OR COUNTRY NAME:
Las Vegas
LAUNCH INITIATED, HERE'S THE KEY FOR YOUR TROUBLE:
LOOK AT THE PRETTY LIGHTS
Press Enter To Continue
Train Station
The train was also one of the most interesting terminals, when opening it, you're instantly dropped into an application instead of a shell. The immediate thought went to exploitation, but we just need to break out of the menu.
Train Management Console: AUTHORIZED USERS ONLY
==== MAIN MENU ====
STATUS: Train Status
BRAKEON: Set Brakes
BRAKEOFF: Release Brakes
START: Start Train
HELP: Open the help document
QUIT: Exit console
menu:main>
First off I tried running each command to see what it did, then went to HELP to see if there was any more information missing.
Looks like the HELP dropped us straight into a less session! This is nice, so maybe we can run commands in less using a bang.
**STATUS** option will show you the current state of the train (brakes, boiler, boiler temp, coal level) **BRAKEON** option enables the brakes. Brakes should be enabled at every stop and whi le the train is not in use. **BRAKEOFF** option disables the brakes. Brakes must be disabled before the **START** command will execute. **START** option will start the train if the brake is released and the user has the co rrect password. **HELP** brings you to this file. If it's not here, this console cannot do it, unLESS you know something I don't. Just in case you wanted to know, here's a really good Cranberry pie recipe: Ingredients 1 recipe pastry for a 9 inch double crust pie 1 1/2 cups white sugar 1/3 cup all-purpose flour 1/4 teaspoon salt 1/2 cup water 1 (12 ounce) package fresh cranberries 1/4 cup lemon juice 1 dash ground cinnamon 2 teaspoons butter Directions: !bash !done (press RETURN) conductor@bb56a879c8fa:~$ ls -la total 40 drwxr-xr-x 2 conductor conductor 4096 Dec 10 19:39 . drwxr-xr-x 6 root root 4096 Dec 10 19:39 .. -rw-r--r-- 1 conductor conductor 220 Nov 12 2014 .bash_logout -rw-r--r-- 1 conductor conductor 3515 Nov 12 2014 .bashrc -rw-r--r-- 1 conductor conductor 675 Nov 12 2014 .profile -rwxr-xr-x 1 root root 10528 Dec 10 19:36 ActivateTrain -rw-r--r-- 1 root root 1506 Dec 10 19:36 TrainHelper.txt -rwxr-xr-x 1 root root 1588 Dec 10 19:36 Train_Console conductor@bb56a879c8fa:~$ grep -ri 'pass' . ./Train_Console:PASS="24fb3e89ce2aa0ea422c3d511d40dd84" ./Train_Console: read -s -p "Enter Password: " password ./Train_Console: [ "$password" == "$PASS" ] && QUEST_UI D=$QUEST_UID ./ActivateTrain || echo "Access denied" ./TrainHelper.txt:**START** option will start the train if the brake is released and t he user has the correct password. conductor@bb56a879c8fa:~$ ./ActivateTrain
Looks like we have the pass now, but we don't even need it with ActivateTrain! :)
MONTH DAY YEAR HOUR MIN
+-----+ +----+ +------+ O AM +----+ +----+ DISCONNECT CAPACITOR DRIVE
| NOV | | 16 | | 1978 | | 10 |:| 21 | BEFORE OPENING
+-----+ +----+ +------+ X PM +----+ +----+ +------------------------+
DESTINATION TIME | |
+-----------------------------------------+ | +XX XX+ |
+-----------------------------------------+ | |XXX XXX| |
| +-+ XXX XXX +-+ |
MONTH DAY YEAR HOUR MIN | XXX XXX |
+-----+ +----+ +------+ O AM +----+ +----+ | XXXXX |
| JAN | | 06 | | 2017 | | 05 |:| 05 | | XXX |
+-----+ +----+ +------+ X PM +----+ +----+ | XXX |
PRESENT TIME | XXX |
+-----------------------------------------+ | SHIELD EYES FROM LIGHT |
+-----------------------------------------+ | XXX |
| XX+-+ |
MONTH DAY YEAR HOUR MIN | |
+-----+ +----+ +------+ O AM +----+ +----+ +------------------------+
| NOV | | 16 | | 1978 | | 10 |:| 21 | +---------+
+-----+ +----+ +------+ X PM +----+ +----+ |ACTIVATE!|
LAST TIME DEPARTED +---------+
Press Enter to initiate time travel sequence.
--->Activating TIME TRAVEL sequence NOW.....
***** TIME TRAVEL TO 1978 SUCCESSFUL! *****
Nice! This worked! Transported us into 1978.
I'll be posting the second part soon, with more details about the server exploitation in part 4.